뉴스 & 기능
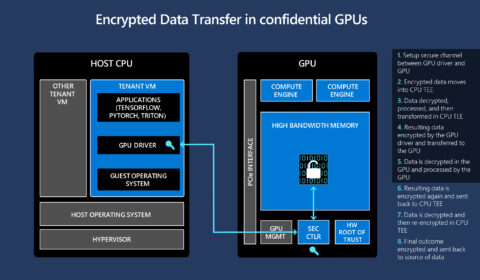
Powering the next generation of trustworthy AI in a confidential cloud using NVIDIA GPUs
| Kapil Vaswani, Antoine Delignat-Lavaud, Stavros Volos, Cédric Fournet, 그리고 Manuel Costa
Cloud computing is powering a new age of data and AI by democratizing access to scalable compute, storage, and networking infrastructure and services. Thanks to the cloud, organizations can now collect data at an unprecedented scale and use it to…
뉴스에서 | Calastone
Calastone announces strategic partnership with Microsoft
Calastone, the largest global funds network, has signed a partnership agreement with Microsoft, which will see the firms collaborate on the use of cloud and distributed ledger technology to create market efficiency across the global investment funds industry. By combining…
Privacy Preserving Machine Learning: Maintaining confidentiality and preserving trust
| Victor Ruehle, Robert Sim, Sergey Yekhanin, Nishanth Chandran, Melissa Chase, Daniel Jones, Kim Laine, Boris Köpf, Jaime Teevan, Jim Kleewein, 그리고 Saravan Rajmohan
Machine learning (ML) offers tremendous opportunities to increase productivity. However, ML systems are only as good as the quality of the data that informs the training of ML models. And training ML models requires a significant amount of data, more…
Microsoft has explained why it’s pursuing ‘safe systems programming’ through efforts like its experimental Rust-inspired Project Verona language and its exploration of the Rust programming language for Windows code written in C++.
뉴스에서 | Microsoft Azure Blog
DCsv2-series VM now generally available from Azure confidential computing
Security and privacy are critically important when storing and processing sensitive information in the cloud, from payment transactions to financial records, personal health data, and more. With the general availability of DCsv2-series virtual machines (VMs), we are ushering in the…

Project Everest: Advancing the science of program proof
| Nikhil Swamy
Project Everest is a multiyear collaborative effort focused on building a verified, secure communications stack designed to improve the security of HTTPS, a key internet safeguard. This post—about the proving methodology and verification tools of Project Everest—is the third in…
어워드 | jStar: towards practical verification for Java
jStar paper wins “Most Influential OOSPLA Paper 2008”

